Have you received a strange email sent to someone with numerous letter h’s in their name? If so, even though you may know the person who has invited you to view the document (and their photo may be displayed), you are seeing a phishing attack. Stop and take a moment before you proceed.
What’s a Phishing Attack?
Phishing is “…the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and, indirectly, money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication” (Wikipedia). That means, even though you see the face of someone you know in the email sharing a Google Doc with you, two things are still possible: 1) Their email has been compromised and 2) They didn’t send you that phishing attack. You can find more information and some helpful infographics about phishing attacks in this blog post by Pixel Privacy. In an earlier blog entry, It’s Not the Phishing, It’s Your Lack of Influence, I pointed out that education is all important when dealing with clever attacks like this. Let’s break down what’s happening.
Scott Laleman (Director of Technology, South San ISD) shares the following:
We’ve blocked mailinator.com in our firewall, filter, and management console, but the messages look like they’re coming from in-house and are “to” an address at mailinator.com (the address with the hhhhhhh in it) with bcc to each person or group, but blocking any messages to or from that domain seems to have stopped them from coming in at this point.
How Do I Avoid the Trap?
But before we do that, let’s ensure you know what your options are in this type of situation:
- When you see a suspicious email asking you to enter your login credentials, you have several options. With Google Docs, simply go to http://drive.google.com and check the Shared With Me section. This will let you know if a document was actually shared with you.
- Open a fresh Compose message and send it to the person who allegedly sent you the message, or call them, tweet them, or Slack them. Ask the question, “Did you share a Google Doc with me?” If the answer is “No,” then delete the document.
- Scrutinize the From: and To: to verify they are authentic.
- If you must click, copy the link to OPEN DOC and create an incognito or private browser window. That way, your login credentials stored in cookies in your browser will not auto-populate or show up in the username/login box. I keep a Firefox browser around for exactly this purpose.
As you will see, each of these steps would have foiled the phishing attack many fell prey to earlier today.
What’s Happening?
At approximately 1:57 pm Central time, users (Update 5/5/17: Google reported, as cited by Threatpost, 1 million user accounts affected) began receiving emails purporting to share a Google document:
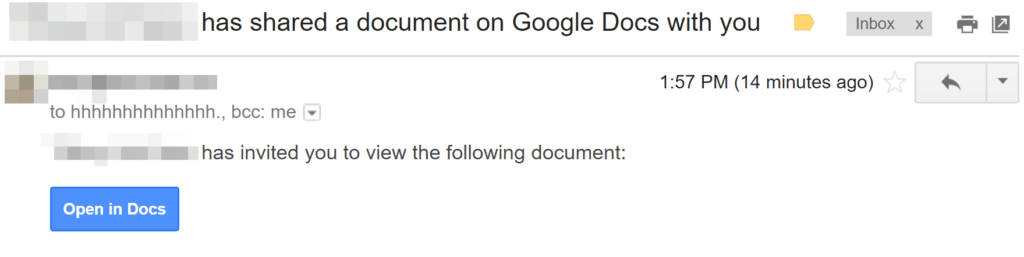
If they clicked on the button shown above, the user was taken to a site that looks like this:
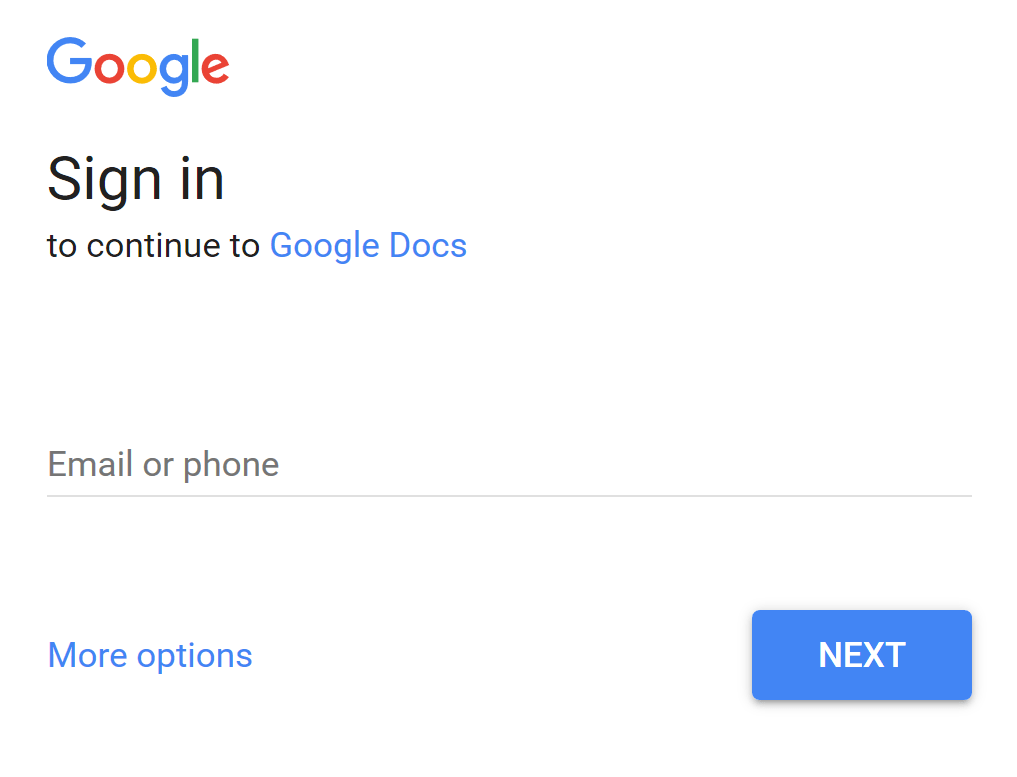
If they entered their email, they would see a screen that pulls in their name and email, then asks for their permission. This is unnecessary for Google Docs, and would normally be a red flag (but most users are unaware that it is).
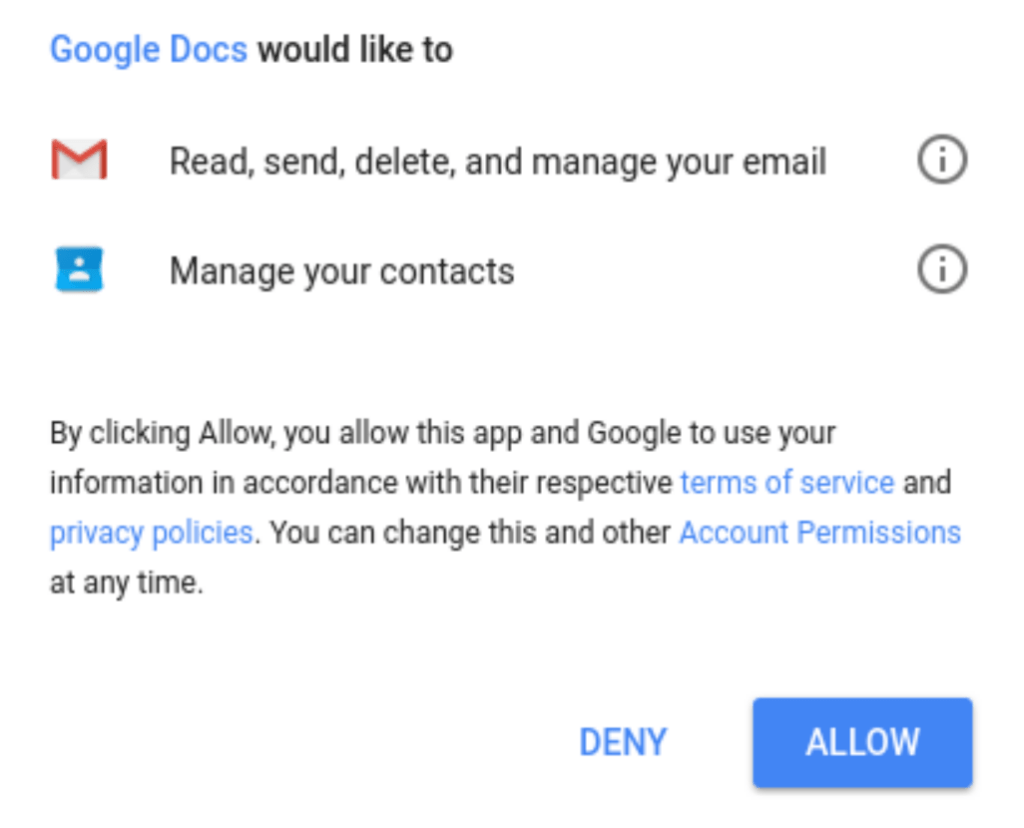
Image Credit: Robert Stubbs, Lockhart ISD
If you were one of the many users snared by this phishing scheme, make sure you follow the steps below to remedy it.
How to Mitigate the Phishing Attack?
If you have fallen for this particular attack, you will need to take the following action:
Go to Apps Connected To Your Account and REMOVE access, as shown in the image below:

Image Credit: Bryce Anderson
Unfortunately, two-factor verification would not have prevented nefarious hackers from accessing your account if you had granted permission. This particular attack has little to do with how you login, and more with how third party apps connect to your Google account.
For a more detailed step by step, check the Reddit Google Forum.
Update 05/05/2017: For school technology administrators, Amplified IT has offered a solution that takes advantage of GAM. “GAM is a command line tool that allows administrators to manage many aspects of their Google Apps Account,” states the GAM Wiki. You can access Amplified IT’s solution online. This solution can only be implemented by your technology administrator and is not intended to be an individual user solution.
What’s Next?
If you haven’t enabled two-factor authentication for your Google Suites for Education domain or begun to educate your staff on how to avoid phishing attacks, then those are your next steps as school district leaders. If you need professional learning on how to accomplish this, don’t hesitate to contact TCEA for assistance.

